Within a short time period of less than 24 hours, cybercriminals have already taken advantage of Monday’s explosion at the Boston Marathon as a newsworthy item. My colleague Mary Ermitano-Aquino noted a spam outbreak of more than 9,000 Blackhole Exploit Kit spammed messages, all related to the said tragedy that killed at least three people and injured many more. Some of the spammed messages used the subjects “2 Explosions at Boston Marathon,” “Aftermath to explosion at Boston Marathon,” “Boston Explosion Caught on Video,” and “Video of Explosion at the Boston Marathon 2013″ to name a few. Below is a spam sample she found:
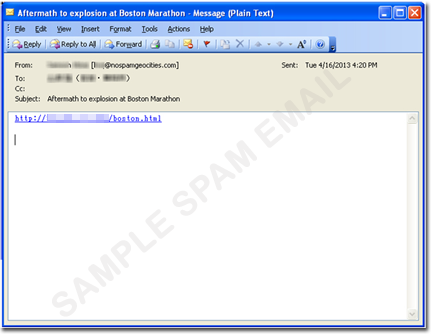
The spammed message only contains the URL http://{BLOCKED}/boston.html , but once you click it, it displays a web page with an embedded video, supposedly from YouTube. At this point, users who click the link may have already downloaded malware unknowingly, aka drive-by-download attacks. Here’s a screenshot of the web page with the embedded video:
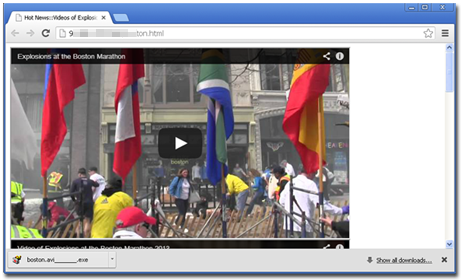
Simply clicking the link in the email triggers an automatic download from the URL http://{BLOCKED}.boston.avi_______.exe. If you’ll notice the lower left-hand corner of the download bar, the file name boston.avi_____.exe is seen as a downloaded file. This is actually a malicious file which happens to be a new variant of WORM_KELIHOS malware.
WORM_KELIHOS.NB routines
Throughout the course of my investigation, I noticed that the IP of the download link varies every time it is accessed. As of this writing, we confirmed that the locations of the IP addresses are found in several countries such as Argentina, Taiwan, Netherlands, Japan, Ukraine, Russia, and Australia. The URL also downloads other similar malware from different links, as seen in the URL log below:
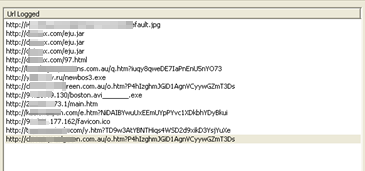
The downloaded samples have the same behavior and same file size, except that it changes the icons used and the file names.
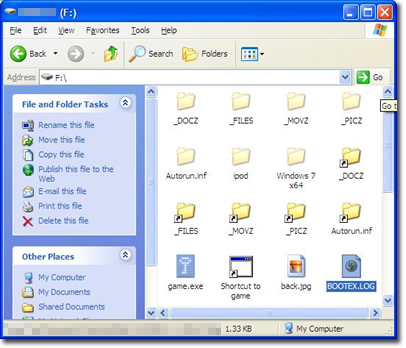
Our analysis also shows that WORM_KELIHOS.NB hides all the directories on the removable drive and replaces them with a .LNK file that uses a folder icon. This executes the malware before it opens that original folder. In addition, it creates .LNK files on infected removable drives with the command C:\WINDOWS\system32\cmd.exe F/c “start %cd%\game.exe. Below is a screenshot of an infected removable drive:
This worm has the capability to steal credentials from the different File Transfer Protocol (FTP) such as LeapFTP, P32bit FTP, FTP Control, SecureFX, BitKinex, FileZilla, and many more. One noteworthy routine about it is that it harvests email addresses from the affected computer’s local drive.
 Spreading like wildfire
Spreading like wildfire
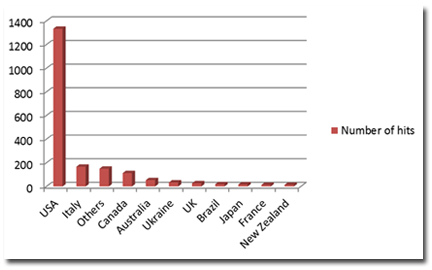
As of today, we have noted a significant number of malicious URLs gathered via the Trend Micro™ Smart Protection Network™ related to the Boston Marathon explosions, with the United States leading the pack among the other countries we monitored.
Aside from the spam sample discussed earlier, we also found that other platforms have also been exploited to spread similar threats. Malicious Tweets and links on free blogging platforms were also crafted just hours after the blast took place.
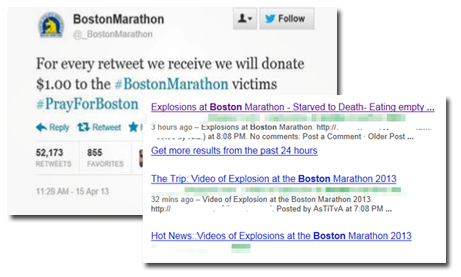 This goes to show that a cybercriminal’s work is never complete. Taking advantage of newsworthy events is indeed a cybercrime staple; each new scheme always seems to vary, which results in a never-ending cycle of malicious mischief.
This goes to show that a cybercriminal’s work is never complete. Taking advantage of newsworthy events is indeed a cybercrime staple; each new scheme always seems to vary, which results in a never-ending cycle of malicious mischief.
We analyzed WORM_KELIHOS.NB further and uncovered that the malware also attempts to steal user’s bitcoin wallet, if stored in the vulnerable system. Bitcoins are known digital currency and are making a wave in today’s IT and threat landscape.
Here is a list of subjects I've seen hit spam traps:
- Subject: 2 Explosions at Boston Marathon
- Subject: Aftermath to explosion at Boston Marathon
- Subject: Arbitron. Dial Global. Boston Bombings
- Subject: Boston Explosion Caught on Video
- Subject: BREAKING - Boston Marathon Explosion
- Subject: Explosion at Boston Marathon
- Subject: Explosion at the Boston Marathon
- Subject: Explosions at Boston Marathon
- Subject: Explosions at the Boston Marathon
- Subject: Opinion: Boston Marathon Explosions made by radical Gays? Really? - CNN.com
- Subject: Opinion: Boston Marathon Explosions - Romney Benefits? - CNN.com
- Subject: Opinion: Boston Marathon Worse Sensation - Osama bin Laden still alive!? - CNN.com
- Subject: Opinion: FBI knew about bombs 3 days before Boston Marathon - Why and Who Benefits? - CNN.com
- Subject: Opinion: Osama Bin Laden video about Boston Marathon Explosions - bad news for all the world. - CNN.com
- Subject:[SPAM] 2 Explosions at Boston Marathon
- Subject:[SPAM] Boston Explosion Caught on Video
- Subject:[SPAM] Explosions at the Boston Marathon
- Subject:[SPAM] Video of Explosion at the Boston Marathon 2013
- Subject: Stiri:EXPLOZIILE de la maratonul din Boston/Spaga este negociata la granita Romaniei/A inventat bautura care INLOCUIESTE MANCAREA/TUNELUL cu mecanisme de NEINTELES al lui STALIN/70 % din infrastructura RCS-RDS este amplasata ILEGAL/BOMBA ANULUI IN SHOWBIZ
- Subject: Video of Explosion at the Boston Marathon 2013
- Here is a list of malicious URLs in those messages (use at your own risk):
- hxxp://109.87.205.222/boston.html
- hxxp://109.87.205.222/news.html
- hxxp://110.92.80.47/boston.html
- hxxp://110.92.80.47/news.html
- hxxp://118.141.37.122/boston.html
- hxxp://118.141.37.122/news.html
- hxxp://176.241.148.169/boston.html
- hxxp://176.241.148.169/news.html
- hxxp://178.137.100.12/boston.html
- hxxp://178.137.100.12/news.html
- hxxp://178.137.120.224/boston.html
- hxxp://178.137.120.224/news.html
- hxxp://188.2.164.112/boston.html
- hxxp://188.2.164.112/news.html
- hxxp://190.245.177.248/boston.html
- hxxp://190.245.177.248/news.html
- hxxp://212.75.18.190/boston.html
- hxxp://212.75.18.190/news.html
- hxxp://213.34.205.27/boston.html
- hxxp://213.34.205.27/news.html
- hxxp://217.145.222.14/boston.html
- hxxp://217.145.222.14/news.html
- hxxp://219.198.196.116/boston.html
- hxxp://219.198.196.116/news.html
- hxxp://24.180.60.184/boston.html
- hxxp://24.180.60.184/news.html
- hxxp://24.214.242.227/boston.html
- hxxp://24.214.242.227/news.html
- hxxp://31.133.84.65/boston.html
- hxxp://31.133.84.65/news.html
- hxxp://37.229.215.183/boston.html
- hxxp://37.229.215.183/news.html
- hxxp://37.229.92.116/boston.html
- hxxp://37.229.92.116/news.html
- hxxp://46.233.4.113/boston.html
- hxxp://46.233.4.113/news.html
- hxxp://46.233.4.113/xxxxx.html
- hxxp://50.136.163.28/boston.html
- hxxp://50.136.163.28/news.html
- hxxp://61.63.123.44/boston.html
- hxxp://61.63.123.44/news.html
- hxxp://62.45.148.76/boston.html
- hxxp://62.45.148.76/news.html
- hxxp://62.45.148.76/xxxxx.html
- hxxp://78.90.133.133/boston.html
- hxxp://78.90.133.133/news.html
- hxxp://83.170.192.154/boston.html
- hxxp://83.170.192.154/news.html
- hxxp://85.198.81.26/boston.html
- hxxp://85.198.81.26/news.html
- hxxp://85.204.15.40/boston.html
- hxxp://85.204.15.40/news.html
- hxxp://85.217.234.98/boston.html
- hxxp://85.217.234.98/news.html
- hxxp://91.241.177.162/boston.html
- hxxp://91.241.177.162/news.html
- hxxp://91.241.177.162/xxxxx.html
- hxxp://94.153.15.249/boston.html
- hxxp://94.153.15.249/news.html
- hxxp://94.28.49.130/boston.html
- hxxp://94.28.49.130/news.html
- hxxp://95.69.141.121/boston.html
- hxxp://95.69.141.121/news.html
- hxxp://95.87.6.156/boston.html
- hxxp://95.87.6.156/news.html
