What computer security threats can we expect to see in 2013?
by Lisa Vaas at Naked Security
Earlier this week, Sophos released the latest edition of its Security Threat Report, summing up the biggest threats seen during
2012, along with five trends that are likely to factor into IT security in the coming year.

Regarding the malware rides we experienced in 2012 and the thrills we can expect in 2013, there will be cross-over, for sure: Blackhole was huge in 2012, and it's not going away, barring the law nailing the person/s running it, the report notes.
Between October 2011 and March 2012, out of all threats detected by SophosLabs, nearly 30% either came from Blackhole directly or were redirects to Blackhole kits from compromised legitimate sites, as Naked Security's coverage of Blackhole exploits attests.
This adroit exploit kit rapidly mutates to thwart security efforts against it, while its software-as-a-service business model is, as the report notes, something for business school grads to drool over.
The professionalization of crimeware such as Blackhole marks a major shift as we head into the new year.
SophosLabs is seeing the ready availability of professionalized, commercialized testing platforms - some that offer money-back guarantees - as laying the foundation for future attacks that give criminals long-term, high-impact access to businesses' data.
This professionalized, consistent poking at businesses' defences will likely turn our attention to layered security and detection across the entire threat lifecycle in the coming year, the report says, as opposed to just focusing on the point of initial entry.
Here are five more trends that SophosLabs anticipates will shape the IT security landscape next year:
Basic web server mistakes.
SQL injection attacks increased in 2012, with large volumes of user names and passwords getting hacked out of web servers and databases. Targets have been both big and small enterprises, motivated by both political and financial ends.
Some of the big ones:
- In May, the website for Wurm Online, a massively multiplayer online game, was shuttered due to an SQL injection while the site was being updated.
- In July, criminals stole 450,000 logins, stored in plain text by Yahoo Voices, using a "union-based SQL injection technique".
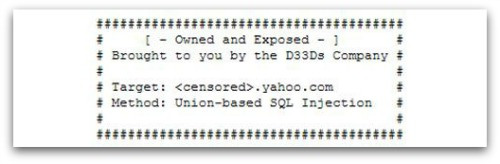
Given the uptick in these credential-based extractions, the report says, "IT professionals will need to pay equal attention to protecting both their computers as well as their web server environment."
More "irreversible" malware.
Ransomware, which encrypts data and holds it for ransom, increased in 2012, and SophosLabs expects to see more in 2013.
The most recent high profile example was in November, when Hacked Go Daddy sites were infecting users.
Unfortunately, the damage can be impossible to repair, the report says:
"The availability of public key cryptography and clever command and control mechanisms has made it exceptionally hard, if not impossible, to reverse the damage."
In 2013, SophosLabs expects to see more such attacks, which should focus IT professionals' attention on behavioral protection mechanisms, as well as system hardening and backup/restore procedures.
Attack toolkits with premium features.
Cybercriminals are investing big in toolkits like the Blackhole exploit kit. That investment has resulted in features such as scriptable web services, APIs, malware quality assurance platforms, anti-forensics, slick reporting interfaces, and self-protection mechanisms.
In 2013, look for continued evolution as such kits pick up premium features that appear to make it a snap to access ever-more comprehensive, high-quality, malicious code.
Better exploit mitigation.
On the plus side, as vulnerabilities increased in 2012 they've become harder to exploit, as operating systems modernized and hardened.
The report also credits ready availability of Data Execution Protection (DEP), address space layout randomization (ASLR), sandboxing, more restricted mobile platforms and new trusted boot mechanisms (among others) for making it tougher to exploit the growing number of vulnerabilities.
Cause for celebration? Well, the report says, we'll probably see crooks just shift over to social engineering to get what they want, from wherever they can get it:
"While we're not expecting exploits to simply disappear, we could see this decrease in vulnerability exploits offset by a sharp rise in social engineering attacks across a wide array of platforms."

Integration, privacy and security challenges.
Mobile devices and applications like social media became more integrated in 2012.
Combine that new coziness with new integrated technologies, such as near field communication (NFC) as well as increasingly clever uses of GPS to pinpoint us in real life, and what you get are new chances for cybercriminals to prey on our security and/or privacy.
It's true for mobile devices, of course, but it doesn't disappear for computing in general, the report says.
In 2013, watch for new attacks built on top of such technologies.
This is just a taste of what's in the report. Download the full Sophos Security Threat Report - it's free, and no registration is required - to learn more.
Beyond that, you can hear more about what 2013 will bring if you sign up for a web seminar about the report that will be held on Tuesday December 11th 2012, at 2pm ET / 11am PT.
SophosLabs expert Richard Wang will be at the web seminar, describing what the coming year might bring, as well as taking a look back over the last year and how attackers extended their reach to new platforms like cloud services and mobile devices, adopted malware toolkits to build smarter attacks, and targeted badly configured websites.
{jcomments on}
