What this infection does:
Antivirus.net is a fake computer anti-virus program that displays false information so that it can scare you into thinking that there is multiple infections in your computer. When installed antivirus.net will be configured to start automatically when you login to Windows. Once started, it will display numerous error messages when you attempt to launch programs or delete files. It will then constantly scan your computer with the program, in turn stating that there are a variety of infections that need to be removed. But the infections cannot be removed until you purchase the program. As this program is a scam do not be scared into purchasing the program when you see its alerts. I have already had a Client that purchased the program and activated, unfortunately his Credit Information has been compromised, not only that but this infection will not remove like others once purchased. If you do purchase this contact your credit companies immediately! The infection also re-configures your internet settings proxy. This will not allow you to connect to any internet service or provider. I will add an article later in order to attempt to show the general public how to fix their proxy settings. So be careful.
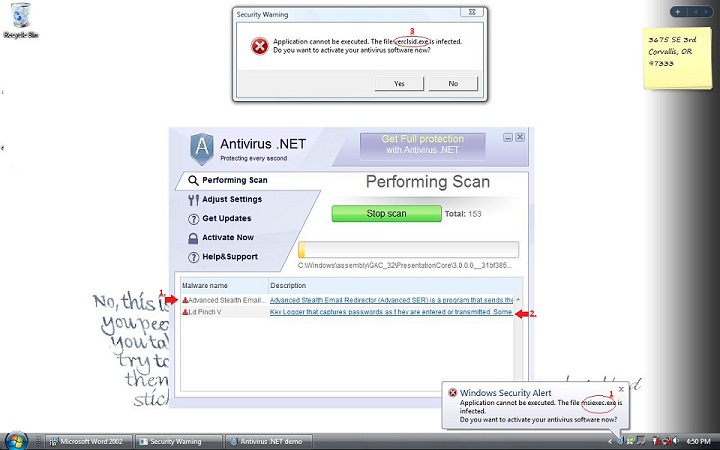
To further make it seem like your computer is not operating correctly, Antivirus .NET will also make it so that certain programs and files on your computer do not execute. When opening these programs, such as mspaint.exe, instead of seeing the program open it will instead display a notification bubble on the bottom right hand side of the screen stating the following. “Window Security Alert Application cannot be executed. The file mspaint.exe is infected. Do you want to activate your antivirus software now?” It will also make the program display a prompt window stating the same. Ignore these notifications, if the user does attempt to click “Activate anti-virus software now” it will re-route them to a page where the infection asks for credit card information. The creators of this infection programmed the infection to display this message to it seem like there is further corruption with your Operating system.
Antivirus .NET also forces your system to not run any programs on your computer. If you attempt to launch a program it will terminate it and state that the program or hard drive is corrupted. It does this to protect itself from anti-virus programs you may attempt to run and to make your computer unusable so that you will be further tempted to purchase the rogue.
While Antivirus .NET is running it will also display fake alerts from your Windows taskbar. These alerts are designed to further scare you into thinking that your computer has an imminent hardware failure. So ignore the notification balloons displayed from the taskbar.
Just like the fake corruption messages and fake scan results, these alerts are only designed to scare you into purchasing the program.

As you can see, the warnings issued by this program are all fake, and once you realize that, the alerts become more of a nuisance rather than a concern. Therefore, do not purchase Antivirus .NET for any reason, and if you already have, please contact your credit card company and state that the program is a computer infection and a scam and that you would like to dispute the charge. To remove this infection and related malware, client would need a Virus removal along with a Tune up.
Threat Classification:
Rogue Programs & Scareware
Associated Antivirus .NET Files:
%Temp%\<random>
%Temp%\<random>.exe
%Temp%\<random>.dll
%Temp%\<random>.exe
%UserProfile%\Desktop\Antivirus .NET.lnk
%UserProfile%\Start Menu\Programs\Antivirus .NET
%UserProfile%\Start Menu\Programs\Antivirus .NET\Antivirus .NET.lnk
%UserProfile%\Start Menu\Programs\Antivirus .NET\Uninstall Antivirus .NET.lnk
C:\Windows\system32\wbem\WMIADAP.EXE
File Location Notes:
%UserProfile% refers to the current user's profile folder. By default, this is C:\Documents and Settings\ for Windows 2000/XP, C:\Users\ for Windows Vista/7, and c:\winnt\profiles\ for Windows NT.
%Temp% refers to the Windows Temp folder. By default, this is C:\Windows\Temp for Windows 95/98/ME, C:\DOCUMENTS AND SETTINGS\ProfileName\LOCAL SETTINGS\Temp for Windows 2000/XP, and C:\Users\ProfileName\AppData\Local\Temp for Windows Vista and Windows 7.
Files Infected:
c:\Users\ ProfileName \AppData\Local\Temp\ueplyuvrk\waprwtwsjmo.exe (Trojan.Downloader) -> No action taken.
c:\Users\ ProfileName \AppData\Local\microsoft\Windows\temporary internet files\Content.IE5\D5C5LDKO\media[1].rc (Trojan.Downloader) -> No action taken.
Associated Antivirus .NET Windows Registry Information:
Registry Keys Infected:
HKEY_CURRENT_USER\SOFTWARE\ineufbr1v (Malware.Trace)
HKCU\..\Run: [<random>.exe] %Temp%\<random>.exe
HKCU\..\Run: [<random>] %Temp%\<random>.exe
Registry Values Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ivyvinxf (Trojan.Downloader) -> Value: ivyvinxf -> No action taken.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyServer (PUM.Bad.Proxy) -> Value: ProxyServer ->
This is also older but most of the newer infections have been a variant of this infection. This infection was one of the first complex. It showed individuals so many options that made it seem so realistic so its no wonder it pressured a lot of users to surrender their credit card information. As stated in previous articles if you have given your credit information contact your card provider immediately.
Thank you for your time,
Ces Garcia
